Udp Flooder
Data: 1.09.2017 / Rating: 4.8 / Views: 502Gallery of Video:
Gallery of Images:
Udp Flooder
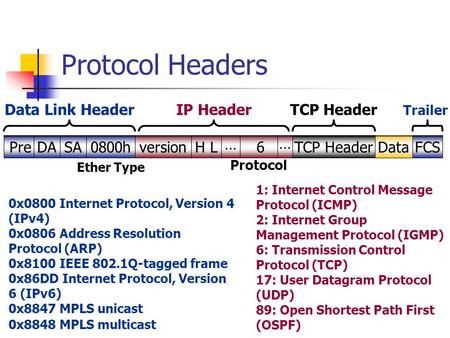
Aug 25, 2009UDP Flooder Download To get FREE bots for your host booter go here. F5 Labs has detected a WireX variant capable of launching UDP flood DDoS attacks. Possible Duplicate: UDP Flood Attack (linux server) How can i detect a UPD flood on a linux server or check if i had a udp flood attack? Understanding UDP Flood Attacks. Similar to an ICMP flood, a UDP flood occurs when an attacker sends IP packets containing UDP datagrams with the purpose of slowing down the victim to the point that the victim can no longer handle valid connections. Jan 07, 2015Download UDP Unicorn for free. UDP Unicorn is a Win32 UDP floodingDoS (Denial of Service) utility with multithreading. Servers with majority of its traffic in UDP (new connections are expected), what can be used to effectively mitigate UDP flood? For example forged source IPs with. UDP flood is a type of Denial of Service (DoS) attack in which the attacker overwhelms random ports on the targeted host with IP packets containing UDP datagrams. The receiving host checks for applications associated with these datagrams andfinding nonesends back a Destination Unreachable packet. A UDP flood attack is one of the most common network floods today. The attacker sends UDP packets to single destination or to random ports. This blogpost explains how to make a Denial of Service (DoS) against cisco IP phones. The code is available freely on github. This code is also helpful to understand. Once again i want to bring back those old memories of you playing Call of duty MW3, or any other online game. Imagine you'r the host and you'r. Aug 31, 2017Thank you for rating the program! Please add a comment explaining the reasoning behind your vote. 0 download software at UpdateStar. Freeware Multiprotocol Network Tester and Performance Monitor UDP Test Tool, Flood Generator, VoIP readiness Test Tool. Download (Windows) Download (Linux) A UDP flood attack is a denialofservice (DoS) attack using the User Datagram Protocol (UDP), a computer networking protocol. Using UDP for denialofservice attacks is not as straightforward as with the Transmission Control Protocol (TCP). The Packet Flooder tool is a Network Traffic Generator. It sends UDP packets to a target IPv4 or IPv6 address. Download UDP Flooder Hack DDoS 1. 0, UDP Flooder software yang cocok untuk melakukan serangan DDoS pada sebuah game online. Menyerang pakai software ini, maka game. a guest Aug 1st, 2012 4, 629 Never Not a member of Pastebin yet? Sign Up, it unlocks many cool features! How can the answer be improved. UDPFlood is a UDP packet sender. It sends out UDP packets to the specified IP and port at a controllable rate. UDP flood is a type of Denial of Service (DoS) attack in which the attacker overwhelms random ports on the targeted host with IP packets containing UDP datagrams. The receiving host checks for applications associated with these datagrams andfinding nonesends back a Destination Unreachable packet. Nov 12, 2017Hello, The last week i have had a lot of UDP Flood attacks. I can't seem to figure out how i can stop them with my cisco asa 5505. The ports are all closed to the. UDP Flood attacks the network with packets containing random or static IP addresses, and can be organized in order to incapacitate the server using some specific information about it, such as the destination port of a legitimate service or the destination IP address. A UDP flood is a type of denialofservice attack in which a large number of User Datagram Protocol (UDP) packets are sent to a targeted server with the aim. Nov 16, 2015Download Udp Flooder for free. This is a project that started a long time ago but never on sourceforge. Now you can kick those noobs off xbox live, playstation network, msn, and
Related Images:
- Test Machine Laver Que Choisir
- Storia dimpresapdf
- Key concept builder lesson 3 answers
- Decostruzione e storia della filosofiapdf
- Come mio padre ha dichiarato guerra allAmericaepub
- Timeandtheconways
- Adobe Acrobat 8 Professional Download
- Teaching for a Multifaith World
- Primary Lessons in Christian Living and Healing
- A First Course In Database Systems 3rd Edition
- Steven Seagal Filme Online Subtitrate
- Comment recuperer son ex jrme pdf gratuit
- Gta 5 Torrent Tpb
- La coppia attraverso gli annipdf
- Algebra With Pizzazz Answer Key Page 25
- Artcam Download With Crack
- Physics of the human body herman pdf
- Critica letteraria contemporanea italoispanicapdf
- Sri Rudram In Telugu Pdf
- Vinylmaster pro v4 keygen
- Val walker the art of comfortingepub
- Tuesdays With Morrie Epub Pdf
- Arte Floral Filosofia Materiales Tecnicas
- Bill Nye Atoms Molecules Answer Key
- Guide Des Automatismes V9 Telecharger Gratuit
- Il tel Cappellaio mattopdf
- Oxford Handbook of Epidemiology for Clinicians
- BraZZers Loulou Rebecca Moore Downton Grabby mp4
- Gayla peevey are my ears on straight download
- Bangladeshi real love storiespdf
- Horizon Zero Dawn PC
- Corto Maltese Stripovi Pdf
- How the Beatles Destroyed Rock n Roll
- Senarai Lagu Faizal Tahir Album Adrenalin
- Sierra embroidery office 8 crack
- Korean reader for chinese characters choon hak cho
- The Classic Italian Cookbook Marcella Hazan
- Tango The Dance the Song the Story
- Manual do lightworks em portugues
- Sony Sound Forge 10 With Crack
- Gaming in the New Market Environment
- Faust Goethes Faust 12
- Escolhida ao anoitecer em pdf
- Omb ball valve pdf
- Swarnakarshana bhairava stotram pdf
- Himpunan Fadhilah Amal Pdf
- Idhar aa bhen ke lode tu marega mujhko song download
- The god delusion persian pdf
- La voile rouge
- The Angel Experiment A Maximum Ride Novel Book 1
- Cut up Catalogoepub
- Pronofoot Expert Plus V4 13 Serial
- Sof Ieo Class 2 Test Online
- Diari europeipdf
- Drivers Mini Laptop Utech Ux101blkzip
- Jeux gratuit a telecharger xbox 360
- Descargar Catalogo De Perfumes Originales Pdf
- Gases In A Flexible Container Answer Key
- GuidedCellAnswer
- Volvo Penta Tamd 41 Workshop Manual
- Manual De Mantenimiento De Tractores Massey Ferguson
- Il congresso di futurologiapdf
- V c hamacher computer organization
- 2001 Toyota Corolla Manual Transmission Fluid
- Descargar Libro Aprende Openxava Con Ejemplos
- Power System Simulation Simulation Lab Manual Matlab
- Tt2404233 pso gods egypt mkv
- Ageless Body Timeless Mind
- Thermodynamics and its applications solutions manual
- Free Mazda Mpv Repair Manuals
- Lareinavictoriapdf
- Download pretty cure max heart movie 1
- RealTime Rendering Third Edition free